A quick guide to setting up a IPv6 Tunnel using public 6to4 relays under GNU/Linux

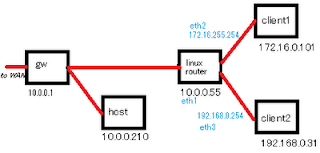
Sett ing up a 6to4 tunnel will allow IPv6 (or dualstack) hosts on network s that only have P ublic IPv4 addresses to access sites and services that are available via IPv 6. The main steps are calculating the IPv6 version of your Public IPv4 address ; establishing a 6 to4 tunnel to one of the free I Pv6 relays available; and configuring the local network to route IPv 6 via th e tunnel . Overv iew of the Topolog y