Netfilter long forgotten
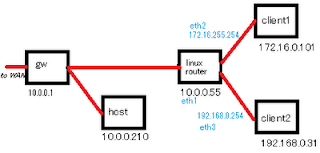
I was lamenting that I'd forgotten far too much about netfilter/iptables so, to jog my memory, I sat down to put together a quick network in VirtualBox. I setup a router/NAT box with one card bridged to my physical network and two cards in two separate Virtual Host-only networks. To keep things nice and distinct, the networks chosen used were 10.0.0.0/24, 172.16.0.0/16 and 192.168.0.0/24.
The simple routing script is below (with all firewall rules removed for brevity):
#!/bin/bash
WAN=eth1
LAN1=eth2
LAN2=eth3
echo 1 > /proc/sys/net/ipv4/ip_forward
# flush everything to being with
/sbin/iptables -F
# setup NAT via $WAN for the two LANs
/sbin/iptables -t nat -A POSTROUTING -o $WAN -j MASQUERADE
/sbin/iptables -A FORWARD -i $WAN -o $LAN1 -m state --state ESTABLISHED,RELATED -j ACCEPT
/sbin/iptables -A FORWARD -i $WAN -o $LAN2 -m state --state ESTABLISHED,RELATED -j ACCEPT
/sbin/iptables -A FORWARD -i $LAN1 -o $WAN -j ACCEPT
/sbin/iptables -A FORWARD -i $LAN2 -o $WAN -j ACCEPT
# inter-LAN routing
/sbin/iptables -A FORWARD -i $LAN1 -o $LAN2 -j ACCEPT
/sbin/iptables -A FORWARD -i $LAN2 -o $LAN1 -j ACCEPT
# make it a policy to drop any traffic not specifically accepted
/sbin/iptables -P FORWARD DROP
When client2 (192.168.0.31) pings a host in the 10.0.0.0 network... :
root@client2:~# ping 10.0.0.210PING 10.0.0.210 (10.0.0.210) 56(84) bytes of data.
64 bytes from 10.0.0.210: icmp_req=1 ttl=127 time=0.724 ms
64 bytes from 10.0.0.210: icmp_req=2 ttl=127 time=1.05 ms
... IPTraf (running on the router) shows traffic being sent/received (10.0.0.55 is the router):
ICMP echo req (84 bytes) from 192.168.0.31 to 10.0.0.210 on eth3ICMP echo req (84 bytes) from 10.0.0.55 to 10.0.0.210 on eth1
ICMP echo rply (84 bytes) from 10.0.0.210 to 10.0.0.55 on eth1
ICMP echo rply (84 bytes) from 10.0.0.210 to 192.168.0.31 on eth3
Removing the NAT section from the script and adding lines for eth1 has the effect of just routing between the three networks if NAT is undesirable:
/sbin/iptables -A FORWARD -i $LAN1 -o $WAN -j ACCEPT/sbin/iptables -A FORWARD -i $WAN -o $LAN1 -j ACCEPT
/sbin/iptables -A FORWARD -i $LAN2 -o $WAN -j ACCEPT
/sbin/iptables -A FORWARD -i $WAN -o $LAN2 -j ACCEPT
As an additional exercise, I setup Squid on the router and changed the maximum_object_size to 1048576 KB then had the two clients and then the router do an apt-get upgrade one after the other. This saves re-downloading packages that have recently been picked up by the other client. Even with just the three boxes it's a decent download saver, but on a larger network it would be essential. I'll probably switch this over to something like app-cacher-ng as it's actually designed with this in mind. Below is the connections shown in IPTraf (top), Squid's access log (left) and the result of running apt-get upgrade (right):



Comments
Post a Comment