Adding 802.1Q Trunking to Debian GNU/Linux
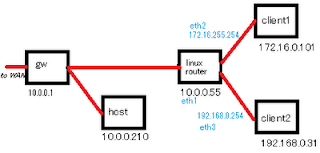
Here's a quick guide to setting up 802.1Q trunking for VLANs on a Debian GNU/Linux box connected to one or more Cisco Catalyst switches, which could then be used as a cheap router replacement. Configuration on the Debian box: Add 8021q to /etc/modules so 802.1Q support is enabled at startup. To install it immediately: # modprobe 8021q Use vconfig to add the VLANs to the interface you'll be using (if vconfig is missing, run apt-get install vlan ): # vconfig add eth0 2 (In the above, eth0 is the physical interface and 2 is the ID of the VLAN) Give the interface an IP. Choose an address in the range you've set aside for that particular VLAN. In this example, VLAN 2 is using 192.168.2.0/24. # ifconfig eth0.2 192.168.2.201 netmask 255.255.255.0